As we all know, technology has been evolving rapidly, especially when it comes to the cloud. “Cloud” is a very special and sometimes confusing term, yet in simplicity, it only refers to a network of remote servers hosted by different cloud providers, offering services to the public for managing data and traditional local networks online. The cloud offers many advantages to everyone, yet issues also arise, especially regarding security. This article will delve into various topics on how the cloud has changed computing as we know it and how different data in the cloud are being stored and managed securely.
ENCRYPTION AND DATA PROTECTION
Importance of Encryption in Cloud Services
Encryption plays a very important role in maintaining confidentiality, as it is the process of converting readable data (plaintext) into a scrambled and purely unreadable format (ciphertext). This ciphertext can only be converted back to its original format by using the right decryption key, a process called decryption.
By applying encryption, data and information stored as well as in transit within the cloud are properly secured and can only be accessed by authorized personnel.
Types of Encryption Algorithms and Their Application in the Cloud
Algorithms in terms of encryption and cryptography define how the encryption and decryption processes are to be carried out. In simple terms, the algorithm is like a lock, while the key is like the key to that lock.
There are three (3) types of encryption algorithms, which are the following along with their application in the cloud:
- Symmetric Encryption – A type of algorithm that uses the same key for both encryption and decryption. The key is shared by both parties and is used to convert plaintext (readable format) into ciphertext (encoded format) and vice versa.
- Popular Algorithms: Advance Encryption Standard (AES), Data Encryption Standard (DES) and Triple DES (3DES)
- Cloud Applications: Symmetric key algorithms are commonly used in various applications like encrypting files and databases that are at rest for long-term archiving and protection as well as securing data in transit, such as in VPNs or wireless networks.
- Asymmetric Encryption – A type of algorithm that uses pairs of keys: a public key, which may be publicly disseminated, and a private key, which is known only to the owner. This algorithm is considered important in modern internet security as it provides a means to securely encrypt data and verify identities in a world where trusting communication channels are not always present.
- Popular Algorithms: RSA (Rivest-Shamir-Adleman) and ECC (Elliptic Curve Cryptography)
- Cloud Applications: With RSA, it is commonly used for secure data transmission, digital signatures, and key exchange in protocols like SSL/TLS. On the other hand, ECC is used to secure messaging, cryptocurrency, as well as SSL/TLS.
- Hybrid Encryption – A type of algorithm that combines the advantages of both symmetric and asymmetric.
- Cloud Applications: Most commonly used in protocols such as SFTP (Secure File Transfer Protocol) and for cloud-based email system. Also used in VPNs, and cloud storage services as well as SSL/TLS.
Key Management and Best Practices for Secure Key Storage
This subsection will focus more on the best-known practices and frameworks for secure key storage such as the following:
- Public Key Infrastructure (PKI) – This is a framework used to create, manage, distribute, use, store, and revoke digital certificates when not needed anymore as well as manage public key encryption. In addition, it facilitates secure electronic transfer of data within the network.
- Digital Signature Standard (DSS) – This uses the Digital Signature Algorithm (DSA) developed by the U.S. National Security Agency (NSA). It generates a digital signature for the authentication of electronic documents.
- Key Escrow – A practice where cryptographic keys are securely stored and managed by a third party under certain conditions.
- Trusted Platform Module (TPM) – A type of special hardware component designed to secure hardware by integrating cryptographic keys within the hardware device itself.
- Secure Enclave – A secure enclave provides a secure space within the device where sensitive data, such as cryptographic keys, can be stored. It is isolated from the main operating system and processor for added security.
- Hardware Security Module (HSM) – This is a physical device that provides secure cryptographic processes.
Data Protection Strategies to Safeguard Sensitive Information
Below are some of the best techniques for safeguarding sensitive information:
- Steganography – This is the practice of hiding or concealing a message, file, or image within another image or file. This can be in the form of an image, audio, video, or text.
- Salting – This is a technique that enhances the security of stored passwords or other sensitive data, such as encryption/cryptographic keys. It involves adding a unique, random string of characters, known as a “salt,” to each password or key string before it is hashed and stored.
- Data Obfuscation – This is the process of disguising sensitive information to better secure it. This can take the form of data masking, encryption, or tokenization.
IDENTITY AND ACCCESS MANAGEMENT (IAM)
Although cloud computing has become so popular, vulnerabilities within its environment also arises such as insufficient identity, credential and access management.
IAM Principles and Concepts in Cloud Environments
There are lots of concepts when it comes to IAM in Cloud Environments. Below are some of them:
- Identity Proofing – This is simply verifying the individual’s identity if they are who they claim to be.
- Provisioning User Accounts – This refers to the process of creating a new user with their accompanying appropriate access rights.
- De-provisioning User Accounts – The process of removing and disabling user accounts with their accesses when no longer needed
- Permission Assignments – The process of assigning of user rights to specific user/s.
- Single Sign-On (SSO) – This refers to a great feature where a user can just log in only once and will have access to multiple resources / systems.
- Lightweight Directory Access Protocol (LDAP) – A popular protocol used for accessing and maintaining directory services.
- Federation – A process of linking identities across different systems/organization boundaries, as well as managing those identities.
- Security Assertion Markup Language (SAML) – An open standard much like as SSO where it allows users to login multiple accounts with one set of credentials.
- OAuth – An open standard for access delegation commonly used for authorizing third party apps to access user’s data securely.
- OpenID Connect – An identity layer on top of OAuth 2.0. Used in modern web apps and mobile apps.
Role-Based Access Control (RBAC) and Its Advantages
Access controls refer to the mechanism and policy used to manage and restrict access to resources in an information system or environment. Types of access controls are Discretionary Access Control (DAC), Mandatory Access Control (MAC), Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC). The most common used one is the RBAC where permissions are assigned based on user’s role within the organization.
RBAC’s common use case are in corporate environments where roles define job functions and access needs which is very straightforward. This access control streamlines access management especially if an organization has many users and roles.
Multi-Factor Authentication (MFA) and Its Role in Strengthening Security
Multifactor Authentication (MFA) is a security mechanism that requires more than one method of authentication from independent categories of credentials to verify the user’s identity. By incorporating MFA, security will increase significantly.
These categories of credentials may vary: something the user knows (passwords, PINs, answers to security questions), something they have (physical smart cards, security tokens), something they are (biometrics), and somewhere they are (GPS location).
IAM Challenges and How to Address Them
As we all know, weak authentication processes, inadequate credential management, and insufficient access controls can lead to unauthorized access to cloud resources. An attacker, whether expert or not, gaining access to a user’s cloud account can manipulate data, eavesdrop on transactions, redirect clients to illegitimate sites, or disrupt services.
While a lot is at stake when dealing with the cloud, there are many solutions to address these challenges. One of the best ways is to apply a ‘Layered Security’ approach, which means using or practicing multiple security standards to protect an organization.
NETWORK SECURITY IN CLOUD ENVIRONMENTS
There are many cloud-specific vulnerabilities such as cloud data breaches, weak access management, insecure interfaces, system vulnerabilities and account hijacking. It is a must for a security professional to understand and be familiar with them as well as the network and cloud environment as a whole.
Understanding Cloud Network Infrastructure
Cloud infrastructures can be complex and might contain system vulnerabilities. The complexity may vary depending on the size of the organization. These vulnerabilities can be exploited by attackers to gain unauthorized access or disrupt services if left unnoticed.
It is important for a security professional to be familiar with all aspects of the cloud to defend the organization and its data securely. You cannot defend if you are not familiar with the environment or the battlefield, as they say.
Securing Data in Transit with SSL/TLS
SSL/TLS plays a big part when it comes to Confidentiality of data in the cloud. By using secure protocols like SSL/TLS, data transmission (data in transit) can be protected securely.
SSL/TLS operates at the transport layer (Layer 4 of the OSI model). There are lots of uses for SSL/TLS such as web browsing on the Internet, protecting Email Communication, encryption algorithms, user accessing VPNs and many more.
As seen on the figure below, the SSL Handshake, SSL/TLS protocol ensures the security and confidentiality of data as it travels across the network.
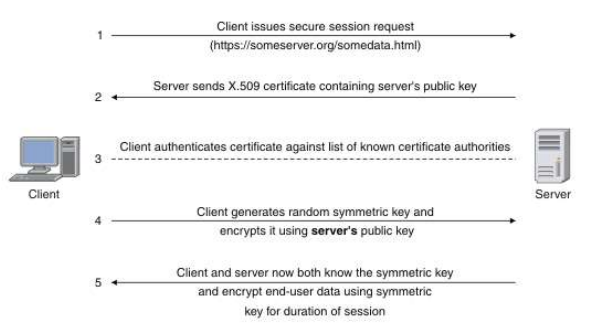
(https://www.ibm.com/docs/en/cics-tg-zos/9.1.0?topic=ssl-how-connection-is-established)
Figure 1: SSL Handshake
Virtual Private Cloud (VPC) and Its Role in Isolating Resources
Extending the capabilities and advantages of Virtual Private Networks (VPN) and Virtual Private Servers (VPS), Virtual Private Cloud (VPC) offers a more scalable cloud services and extensive cloud network controls and on top of that, a more custom network configuration. Moreover, and most importantly, it also offers a more secure network connection by isolating resources that might be crucial for remote access to a corporate network.
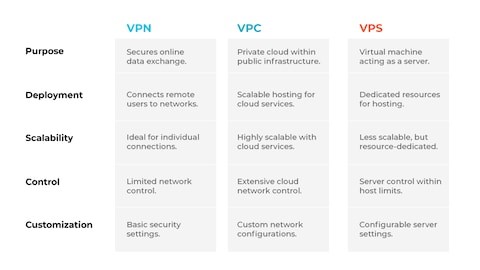
Figure 2: VPN vs. VPC vs. VPS
(https://www.paloaltonetworks.com/cyberpedia/vpn-vs-vpc-vs-vps)
DDoS Mitigation Techniques for Cloud Environments
Even cloud-based network/systems are not safe with Distributed Denial of Service (DDoS) where its main goal is to disrupt Availability. The good news is, there are lots of mitigation techniques that can be implemented to combat it. Below are some of those great techniques and practices:
- Penetration Testing – Allowing DDoS attacks in the Rules of Engagement can help identify vulnerabilities and prevent them.
- Security Playbooks – Playbooks are sets of procedures and detailed steps to respond to an incident. They can cover a range of scenarios, from responding to a data breach to mitigating a DDoS attack.
- Traffic Filtering and Rate Limiting – Implementing filters using virtual firewalls to block malicious traffic as well as setting up a rate limit to control the amount of traffic reduces the impact of DDoS attacks.
- Autoscaling – This refers to dynamically allocating additional resources/bandwidth that can properly absorb the bulk traffic load during a DDoS attack.
- Content Delivery Networks (CDNs) – This refers to the distribution of contents across multiple servers globally over the network to reduce the load on the main server.
- Load Balancers – These are devices or software that evenly distribute traffic across multiple servers preventing any single server from being overloaded.
- Web Application Firewalls (WAFs) – WAFs are specifically designed to protect web applications by filtering and monitoring HTTP traffic between a web application and the Internet; usually prevents SQL Injection, XSS, and session hijacking.
- Failover Mechanism – Provides a reliable backup in case the primary cloud-based load balancer/system/server fails, ensuring continuity of service.
SECURITY MONITORING AND INCIDENT RESPONSE
It is very important to note that cloud computing involves a shared responsibility model where security obligations are divided between the cloud provider and the client.
Cloud Security Monitoring Tools and Techniques
Cloud infrastructure monitoring refers to overseeing the entire IT infrastructure of an organization within the cloud, including cloud services and other critical infrastructure elements.
The primary goal is to ensure the cloud infrastructure’s integrity, availability, and performance. This includes identifying potential security threats like network breaches, unusual traffic patterns, or attempts to access restricted areas of the network.
Some critical monitoring activities are:
- Log Aggregation – Collecting and consolidating logs across the entire cloud network.
- Alerting – Notifying administrators/security team about security incidents.
- Scanning – Identifying vulnerabilities or any misconfigurations and weaknesses within the network.
- Reporting – Generating reports regarding the security status of the organization.
- Archiving – Securely storing important data for future reference.
- Quarantine – Isolating affected systems or components to prevent the further spread of threats.
- Alert Tuning – Refining alert mechanisms to reduce false positives and the like.
Identifying and Responding to Security Incidents in Real-Time
When it comes to cybersecurity threats within the cloud, responsiveness or the ability to detect and respond to security threats rapidly is crucial. A responsive cloud architecture can significantly reduce the impact of security breaches. Automation and ticket creation also plays a crucial role as it can detect anomalies or issues and generate tickets automatically, ensuring that potential security incidents are promptly recorded and addressed.
Handling a security incident typically involves several key steps, designed to effectively identify, manage, and mitigate the incident.
◦ Preparation – Having a plan in place to quickly respond if necessary. Includes Incident Response Plan, Incident Response Policy and Training.
◦ Detection – Identifying potential security incidents.
◦ Analysis – Refers to determining the type of attack, the systems affected, the data compromised, and the attacker’s tactics, techniques, and procedures (TTPs).
◦ Containment – Aims to limit the scope and magnitude of the incident.
◦ Eradication – The goal is to eliminate the threat from the environment entirely.
◦ Recovery – This is where affected systems and services are restored to normal operations.
◦ Lessons learned – Documented; main objective is to improve the incident response plan and other security measures.
Security Information and Event Management (SIEM) Solutions
Security Information and Event Management (SIEM) tool is crucial for detecting, understanding, and responding to security incidents. It is used for Log management, event correlation, alerting and reporting.

Figure 3: How SIEM Works
(https://qph.cf2.quoracdn.net/main-qimg-536b4de23f8430c75ba343757ffbd04f-pjlq)
Developing an Effective Incident Response Plan
When it comes to incident response planning, having a clear plan for responding to detected impersonation attempts, including isolating affected systems and changing compromised credentials, and other forms of threats, is very important. This is the foundational stage where organizations develop incident response policies, establish incident response teams, and set up necessary tools and communication channels. The ability to detect and respond to security threats rapidly is crucial.
COMPLIANCE AND LEGAL ASPECTS
Internal audits play a critical role in ensuring that the organization complies with relevant cybersecurity regulations and standards. Non-compliance can result in significant legal penalties, including fines and sanctions.
Overview of Cloud Compliance Standards
Most organizations using the cloud deals with regulated data, which refers to the data that is subject to regulatory requirements, such as personal data protected under laws like General Data Protection Regulation (GDPR), health information covered by Health Insurance Portability and Accountability Act (HIPAA), or financial data under Payment Card Industry Data Security Standard (PCI-DSS). Adhering to such Regulations ensures security integrity and avoiding the negative consequences of non-compliance for such organizations.
Challenges in Cloud Compliance and How to Overcome Them
Global legal implications come into play for organizations operating internationally or dealing with data across national borders. Organization must navigate various international laws and regulations, such as the General Data Protection Regulation (GDPR) in the European Union, CCPA in California, and various other data protection regulations globally that has extraterritorial reach. Global compliance is complex due to the variation in laws across different countries and regions.
Overcoming Cloud Compliance Challenges:
Regular Internal Audits and Compliance Monitoring play a critical role in ensuring that the organization complies with relevant cybersecurity regulations and standards. By regularly reviewing and assessing internal processes and controls, the organization can identify and rectify compliance gaps before they become a legal or security issue.
Legal Responsibilities of Cloud Service Providers and Customers
It is always important to note that both cloud service providers and customers share the responsibility of ensuring a secure and compliant cloud environment. Cloud service providers must ensure secure and reliable services that comply with legal standards, while cloud customers must also fulfill their responsibilities such as data governance, access management, data encryption, incident response, vendor management, and backup and recovery.
Data Sovereignty and Its Impact on Cloud Security
For organizations operating internationally, global security considerations are critical. This includes understanding and complying with the cybersecurity laws and regulations of all the countries in which they operate. Global considerations also involve dealing with cross-border data transfers and multinational regulatory compliance.
In summary, it is indeed that cloud computing will continue to grow in the following years without showing any signs of lagging. As these types of technological advances grow, different types of new and hybrid threats are also developing along with them. It is important for security professionals to always stay updated with the latest security news, not just within the cloud environment. While threats will always be present, the good news is that there will also be many solutions and mitigation strategies to combat these threats.
All we have to do is our Due Diligence.